Comprehensive email security that adapts to your context
Other email security solutions operate like black boxes, filtering and analyzing emails without offering real insight into their decision-making, leaving you to merely react to past attacks. With xorlab, you get a platform that continuously learns and automatically adapts security policies to stop new and evolving threats at first sight.
Proactive
Automatically filter emails based on their risk relative to your context.
Contextual
Gain visibility into communication patterns and relationships.
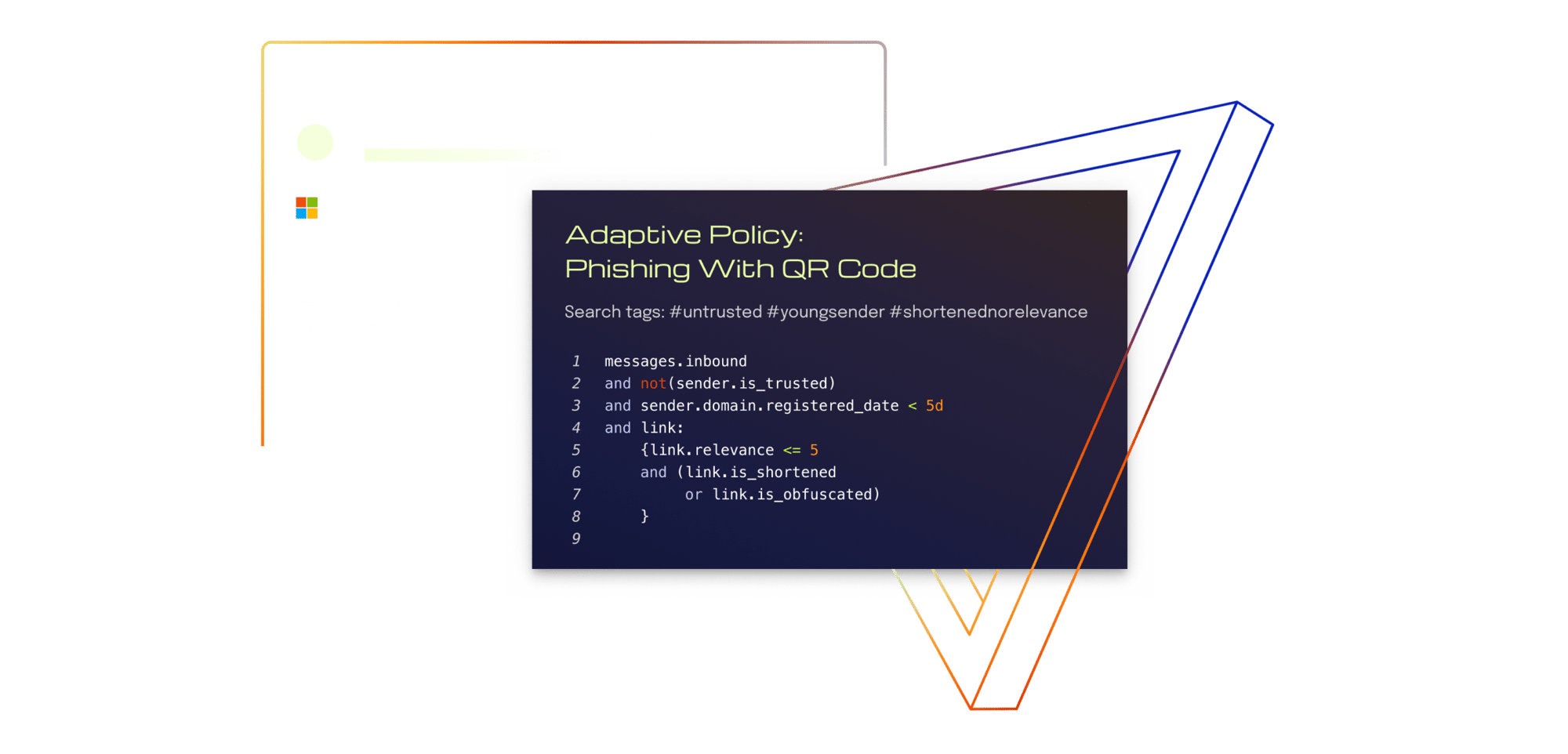
Adaptive
Continuously minimize email attack surface with adaptive security policies.
Effortless
Automatically analyze and triage internal email incident reports.
Integrating xorlab into our security stack has been a game-changer. xorlab's advanced, relationship-driven threat detection not only stops yet unidentified threats but also consistently exhibits an exceptionally low rate of false positives.

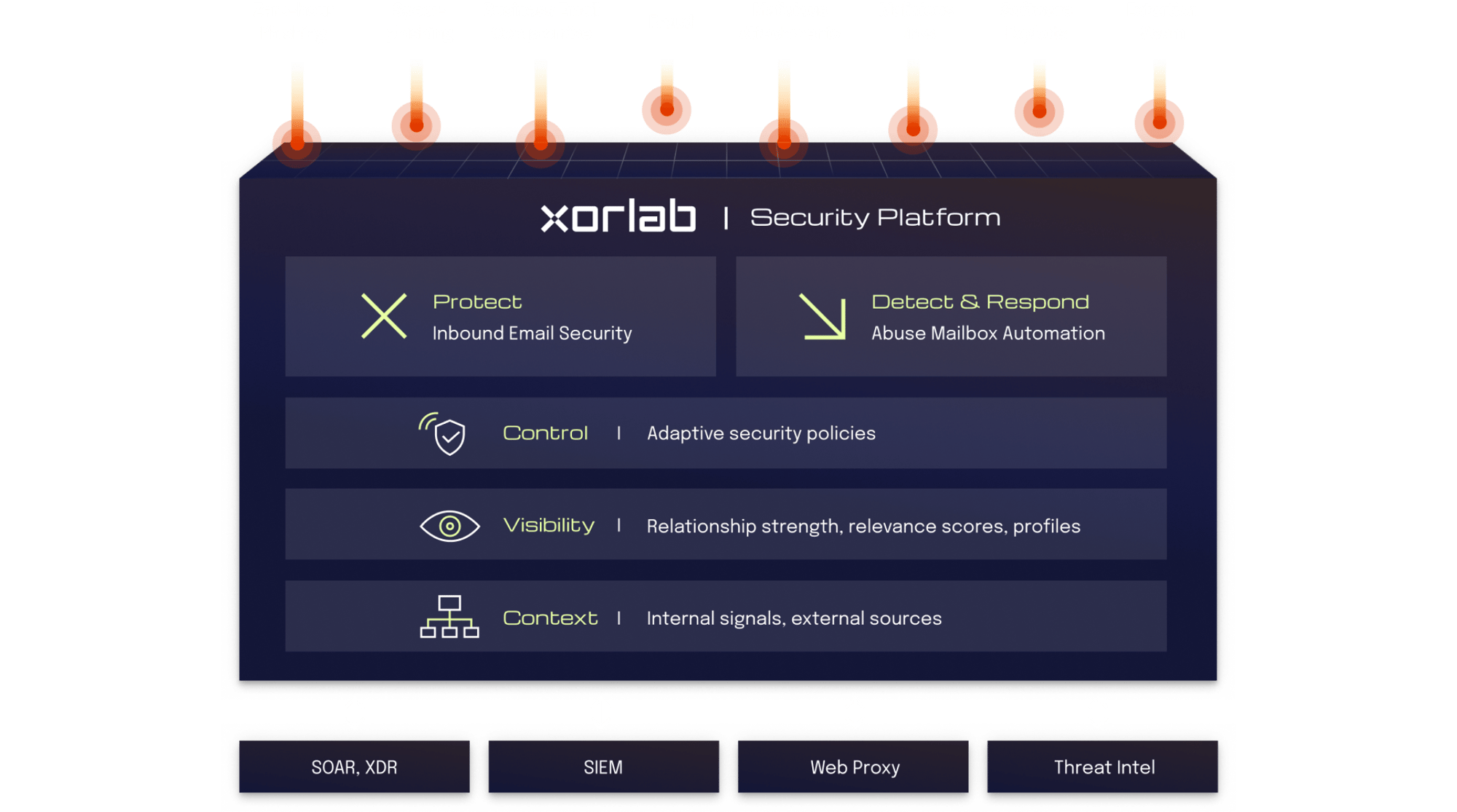
The email security platform that evolves with you
Your all-in-one platform to automatically reduce attack surface, minimize third-party vendor risk, and stop zero-hour email threats. Whether your email is cloud, hybrid, or on-prem, we’ve got you covered.
xorlab with its rich user interface provides us with the necessary insights to our daily email traffic and empowers us to immediately react to new threats. Fast searching capabilities and a powerful filtering engine allow for quick analysis and a target-oriented response.






