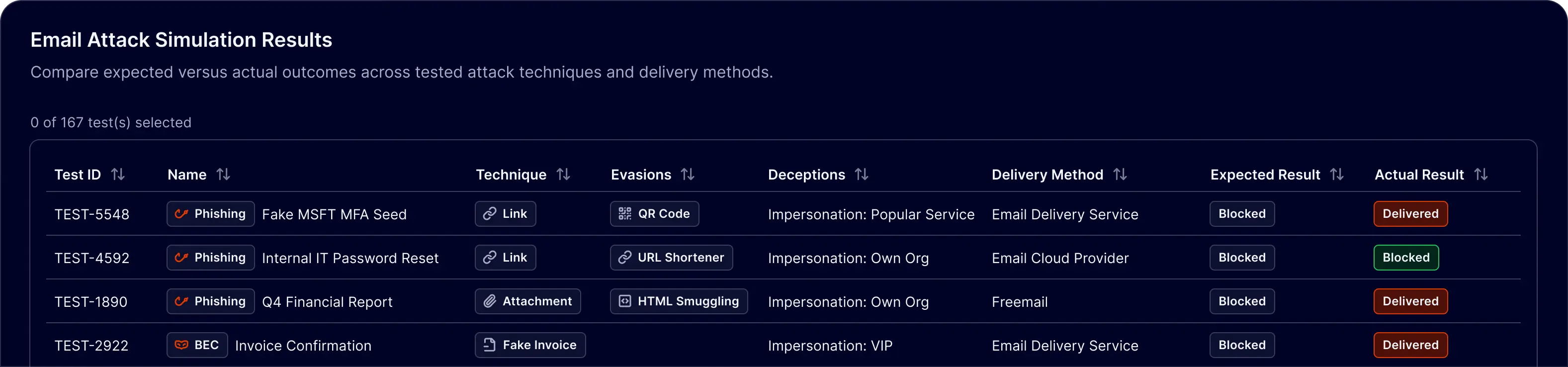
Uncover gaps before attackers do
And fix them fast. With more than 160 attack scenarios across phishing, BEC, malware, and extortion scams, our simulation shows you exactly with which techniques attackers can bypass your stack and where tuning is needed.