CVE-2025-8088: How xorlab stops this WinRAR zero-day before it hits the inbox
CVE-2025-8088 is a newly disclosed zero-day vulnerability in WinRAR’s file parsing logic that enables attackers to manipulate extraction paths and place malicious files in sensitive system locations, allowing arbitrary code execution. All it takes is for a user to extract the crafted archive—making email delivery an ideal vector. According to researchers, threat actors are already weaponizing this flaw in active campaigns. The vulnerability has a CVSS of 8.4 and a risk rating of high. Since its discovery a patch has been made available in version 7.13.
Understanding the threat
This exploit presents several distinct risks to targeted companies:
Technical stealth and persistence. CVE-2025-8088 is a directory traversal flaw in the Windows versions of WinRAR and related utilities before version 7.13 Final. It lets attackers bypass intended extraction paths and drop malicious files—such as .lnk shortcuts or DLLs—into locations like the Windows Startup folder. These payloads then execute automatically on the next login, granting remote code execution without further user action.
Social engineering to increase success rates. Adversaries, as for example the RomCom group, send weaponized .rar archives through spear phishing campaigns disguised as job applications or official documents. This familiar pretext encourages recipients to open the archive, unknowingly triggering the exploit.
Threat actor capability and intent. RomCom—also tracked as Storm 0978, Tropical Scorpius, Void Rabisu, and UNC2596—is a sophisticated, Russian aligned cyber espionage group. Their operations target governments, critical infrastructure, financial, manufacturing, defense, logistics companiesand NGOs, and they have a track record of exploiting zero days across multiple platforms, underscoring their adaptability and depth. The end goal of the current campaign was to download a backdoor. There are indications that this vulnerability might have been sold in June in underground forums for $80’000.
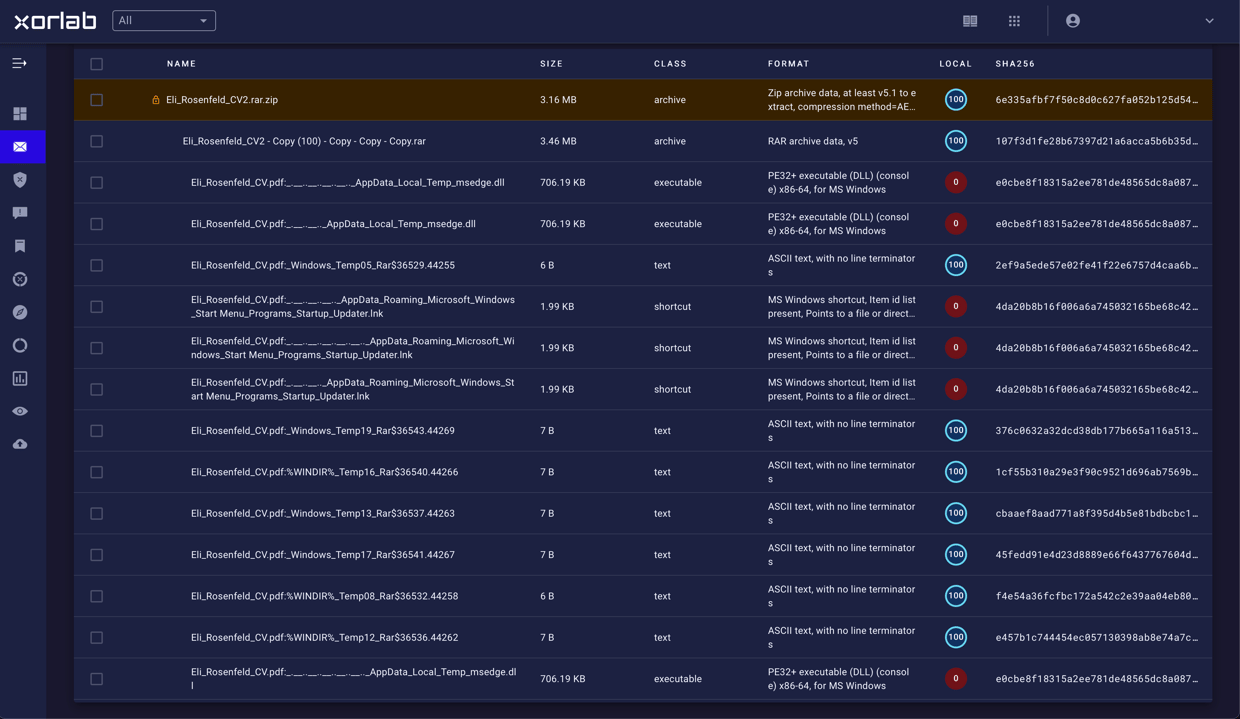
How xorlab stops CVE-2025-8088 out of the box
xorlab email security detects this attack before the malicious archive reaches the inbox—proactively and without relying on prior threat intelligence. In our internal testing with a live sample, the system automatically quarantined the email based on the nonexistent sender‑recipient relationship and the presence of executable file types inside the archive. Our archive analysis process was not vulnerable to the CVE‑2025‑8088 technique and consistently revealed hidden files, preventing the kind of stealthy file placement this exploit depends on.
Key detection factors included:
- Identification of suspicious attachment types (.rar) combined with executable payload indicators (.lnk, .DLL)
- Contextual risk scoring based on deviation from established sender behavior
- Policy triggers linked to known attack surfaces, in this case executable content
The result: the malicious email never reached the target user, eliminating the risk of exploitation. Our archive analysis was not vulnerable and always showed hidden files.
Analyst takeaways
- Zero‑days like CVE‑2025‑8088 demand inline defenses that block threats before inbox delivery.
- Social engineering lures combined with trusted file formats make traditional signature‑based solutions insufficient.
- Context‑aware detection, such as relationship‑based scoring, significantly reduces the risk from novel exploits.
- Timely patching is critical—WinRAR users must manually update to version 7.13 or later to close this vulnerability.
YARA rule for detection
Below is a YARA rule (developed by Arnim Rupp) that security teams can use to check if their systems have been exposed to this specific exploit pattern:
<!-- The yara rule also checks zip files, not only rar. So let's be generous with the file type here: -->
<fileType equals="archive"/>
<yaraMatch>
<!-- Based on https://github.com/Neo23x0/signature-base/blob/master/yara/exploit_rar_archive_with_path_traversal_aug25.yar -->
<yaraRule>
rule EXPL_RAR_Archive_with_Path_Traversal_Aug25 { meta: description = "Detects RAR archives abused for path traversal like CVE-2025-8088 and CVE-2025-6218" reference = "https://www.welivesecurity.com/en/eset-research/update-winrar-tools-now-romcom-and-others-exploiting-zero-day-vulnerability/#the-discovery-of-cve-2025-8088" author = "Arnim Rupp (Nextron Systems)" date = "2025-08-11" score = 70 hash = "2a8fafa01f6d3863c87f20905736ebab28d6a5753ab708760c0b6cf3970828c3" hash = "dfab2f25c9d870f30bbc4abb873d155cf4904ece536714fb9cd32b2e0126dfab" hash = "107f3d1fe28b67397d21a6acca5b6b35def1aeb62a67bc10109bd73d567f9806" strings: // Only look for the users Autostart folder because the most effective attack method // Use \ and / to handle archives created on Windows and Linux $s1 = "..\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu" $s2 = "../AppData/Roaming/Microsoft/Windows/Start Menu" // CVE-2025-6218: $s3 = "/.. /AppData/Roaming/Microsoft/Windows/Start Menu" $s4 = "/.. ./AppData/Roaming/Microsoft/Windows/Start Menu" $s5 = "\\.. .\\AppData\\Roaming\\Microsoft\\Windows\\Start Menu" condition: 1 of ( $s* ) and ( uint16(0) == 0x4B50 // Yes, Winrar can choke on ZIPs or int32(0) == 0x21726152 // RAR ) }
</yaraRule>
</yaraMatch>

