How to Protect Businesses against Ransomware Attacks

One of the most prevalent cyber threats today, ransomware attacks are becoming more severe and sophisticated. In 2021, SonicWall recorded a 148% surge in global ransomware attacks, taking the overall count to 495 million. The numbers make last year the worst the company has ever recorded.
To protect against ransomware attacks, organizations should first focus on prevention and developing and implementing the right strategies to defend themselves. This involves understanding the bases of the attacks, the most common attack vectors, and what makes ransomware attacks successful. Analyzing worldwide known examples from one’s industries and outside of them are also excellent ways to prepare for potential threats.
How Ransomware Attacks Work
There are different types of ransomware attacks, each with its specific details. Still, while there isn’t a one-size-fits-all approach that bad actors use, three key phases apply in most cases.
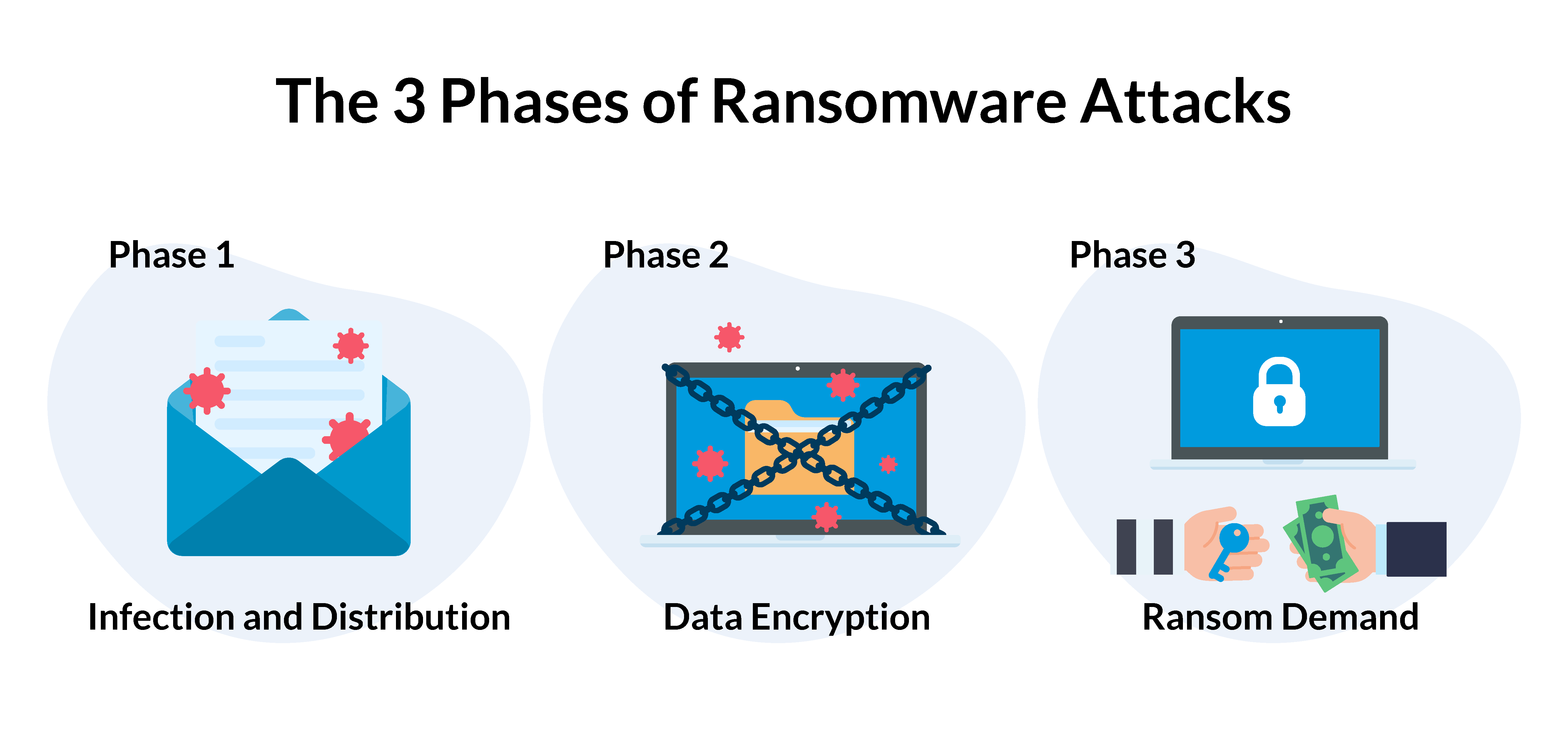
Phase 1: Infection and Distribution
The first phase of a ransomware attack starts with accessing an organization’s network. This may be done in several ways, with phishing emails being the primary method. In this case, cybercriminals send malicious emails with links or attachments that, once accessed, download and execute the malware on the victims’ terminals. It only takes a negligent click to turn the tentative into a costly breach.
Another way to spread infection into the enterprise’s systems, especially in today’s work-from-home landscape, is by taking advantage of the Remote Desktop Protocol. To do so, it is enough for attackers to either steal or guess a target’s login credentials. This is especially easy if potential victims reuse their passwords for multiple accounts or use one of the weak ones that attackers know (e.g., 123456789, 123456, password123, etc.).
Once cybercriminals identify the correct ID/password combination, they can gain remote access to the user’s computer, enabling them to download and execute the malware on the terminal and distribute it across the organization.
Other attempts may include exploiting certain software vulnerabilities. A well-known example here is how the WannaCry ransomware used the Eternal Blue exploit, a software vulnerability in Microsoft’s Windows operating systems (OS) Server Message Block (SMB) version 1 (SMBv1) protocol. The exploit enabled the bad actors to execute arbitrary code and take over a system through specially crafted packages.
Oftentimes, to be successful, most cybercriminals combine multiple ways of infecting networks.
Phase 2: Data Encryption
Once bad actors have gained access to the network, it is time to start the second phase, data encryption. This means that malware encrypts accessible files with a key known solely by the attacker. The encrypted ones replace the old, original files and, in some cases, backups and shadow copies are deleted. Using this approach, cybercriminals ensure that recovering data is even more complicated for organizations.
Phase 3: Ransom Demand
After cybercriminals have encrypted the files, it is time for them to make their demand. This may happen in different ways, depending on the bad actor's approach. One of the most common methods is changing a computer’s background to a ransom note which offers to provide the victim the key to access their files in exchange for cryptocurrency. Another option would be to add text files to the encrypted directories so that, when users open them, they receive the ransom message.
If the organization pays the ransom, the cybercriminal may provide a copy of the encryption key or of the private key that protects the symmetric encryption key, as well as the decryptor program that victims may use to restore access to the original files and the system. All that needs to be done, at this point, is to enter the information into the program.
Although these 3 phases can be found in all ransomware attempts, there are types of attacks that might be different or include additional measures. One relevant example is Maze, the ransomware that uses file scanning, registry information, and data theft before data encryption.
What Are the Most Common Ransomware Attack Vectors?
There are several ways through which an organization can become vulnerable, with cyber attackers preferring the following three.
1. Email Phishing
The most widely used attack vector is email phishing. In this case, attackers use email lists to send malicious links to an organization’s employees. This might seem like a significant effort, but it has become quite simple with software automation. The principle behind the strategy is that it only takes one person to click on the link to enable cyber attackers to infiltrate an entire organization.
As phishing has evolved, bad actors have developed several more efficient approaches. One of the most popular is spear phishing, a version in which cybercriminals use public information about their targets, simulating a relationship between the email sender and the receiver. This is usually done by using information available on social media accounts, like LinkedIn, to create emails that inspire trust, thus increasing the chance of clicking on links or downloading files.
Another form of spear phishing, called whaling, also known as CEO fraud, is directed toward top managerial employees with access to higher-level data. These stakeholders are usually less likely to commit negligence, so it is essential to make messages look like they are coming from a trustworthy source.
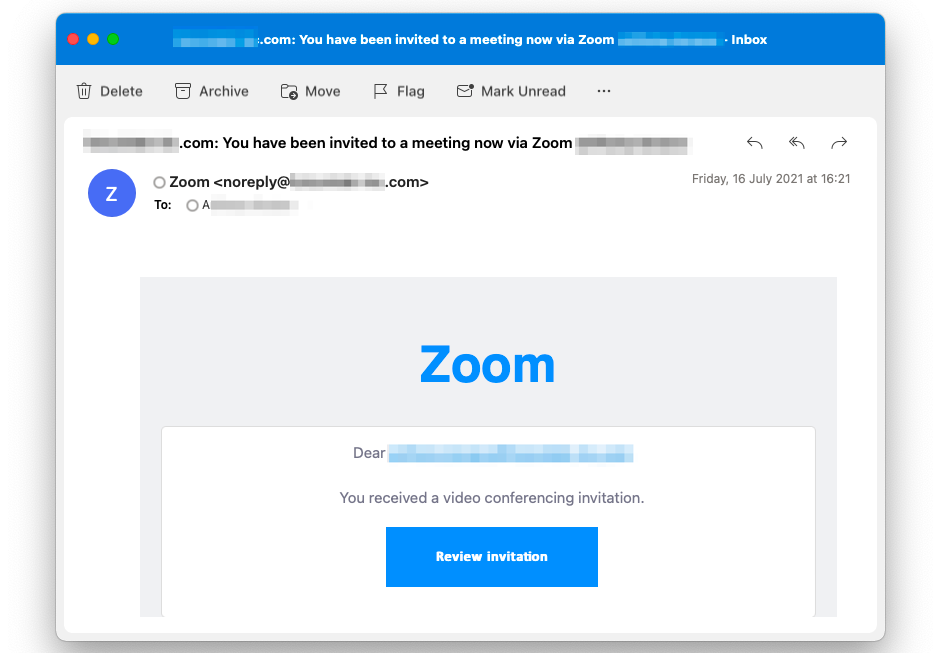
Anonymized screenshot of a fraudulent Zoom meeting invitation. (Source: xorlab)
Top Reasons Why Employees Fall for Spear Phishing
Bad actors don’t focus solely on the technical side of attacks but also emotional factors. Since they need to take advantage of people’s trust, they use social engineering techniques to create emails that make sense from a corporate perspective and have the same tone of voice and format as legitimate messages. They lower victims’ skepticism and increase their chances of a successful spear phishing attempt.
To add that extra layer of emotion that sparks quick actions, bad actors also use keywords meant to suggest urgency. Terms like “immediate action required,” “urgent,” and “overdue notice” not only get the receiver’s attention but also send a solid call to action, demanding for something to be done. Other emails take advantage of people’s vulnerabilities and desires, as they present opportunities that are not real, such as winning a deal, being offered a bonus, or a promotion.
To go even further and remove any doubt for potential victims, bad actors put in the extra effort and adopt an organization’s communication style, focusing on workflows and processes to which employees are accustomed. Cyber attackers study users’ behaviors and correspondence patterns and replicate standard emails that impersonate colleagues, suppliers, or partners.
Another reason why these attempts are particularly successful is because, especially in the corporate environment, employees need to make quick decisions. Opening an email, for example, is often an automatism since users receive tens or even hundreds of messages per day. People check messages, access links, and download attachments while taking phone calls or scheduling meetings. With so much multitasking, it is sometimes just a matter of time before someone makes a mistake.
2. RDP (Remote Desktop Protocol) Compromise
By allowing users to interact with their desktops from remote locations, Remote Desktop Protocol (RDP) offers a high level of convenience to employees from different departments. This solution enables them to enjoy working from home while proceeding with their tasks. Moreover, it is also a preferred choice of IT professionals who only need to connect remotely to access someone’s computer, troubleshoot problems, install updates, etc.
At the same time, this type of solution comes with its share of challenges, as the Remote Desktop Protocol increases an organization’s attack surface. RDP is a significantly important gateway for bad actors.
RDP often goes hand in hand with brute-force attacks through which bad actors use trial-and-error to guess login information and access computers. Another tactic that works for unauthorized RDP access is purchasing credentials on the dark web.
3. Software Vulnerabilities
Replacing legacy software or updating existing tools is a challenge in most companies because employees are often resistant to change. Many organizations still use unpatched software versions. These environments are excellent for bad actors since unpatched vulnerabilities open the door for attacks without requiring any credentials. Zero-day vulnerabilities can be exploited by bad actors to launch an attack, before potential victims have the chance to apply security updates to protect against it.
The Impact of Ransomware across Industries
Healthcare
Healthcare organizations have access to sensitive and personal patient data that they store in their systems. These types of information are particularly valuable and allow bad actors to demand higher ransoms.
In addition, the overall pressure put in recent years on healthcare organizations makes them an extremely attractive target for cybercriminals. Given the massive need for quick measures and patient support, the long hours, and the overall lack of personnel, many employees might overlook cybersecurity procedures. Healthcare professionals are more likely to open malicious emails or click on the wrong links in this context.
One of the most popular and costly cyberattacks in the healthcare industry happened in 2020, when bad actors accessed the database of Universal Health Services (UHS). The organization that, at the time, had over 90,000 employees and 3.5 million patients in the U.S. and the U.K. went through Ryuk ransomware. Due to the attack, UHS couldn’t fully operate for a month, as it couldn’t keep up with the high number of patients. Invoicing was delayed, systems needed to be restored, and additional staff members were brought in to help. The whole incident cost the company around $67 million.
Manufacturing
NTT 2021 figures showcase an increase of 300% in ransomware targeted at companies in the manufacturing sector, making the industry the most susceptible to such attacks. One example is Norsk Hydro, the Norwegian aluminum manufacturer operating in 40 countries worldwide, which suffered a LockerGoga ransomware attack. Due to the incident, the company’s operations were seized, and part of its 35,000 employees and 22,000 devices were put on hold. The whole attack cost the company over $38 million in direct and indirect losses.
Two main aspects attract cybercriminals to manufacturing companies:
- A significant number of IoT devices and specialized equipment managed by software. These create a broad attack surface.
- Pandemic working conditions and limited security flows make factories easy targets for cybercriminals.
Telecommunications
Telecom companies are especially prone to attacks because they offer critical services on which consumers and society in general place much importance. The modern work environments and lifestyles appear to depend on cell service and Internet connection, so any attempt to tamper with these would create significant disruption. Cybercriminals know this and take advantage of the situation to extract some of the largest ransoms in history.
Another aspect that increases attackers' interest in telecom companies is the abundance of personal data with which they interact and which they sometimes store. Examples include names, phone numbers, email addresses, passwords to company-operated platforms, payment information, etc.
One notable attack targeted Orange, Europe’s fourth-largest telecommunications operator. In 2020, the company fell victim to the Nefilim scheme, which gave bad actors access to sensitive data about the company's corporate clients and end-users. To put pressure on the organization’s representatives to accept their demands, cybercriminals posted online some of the data obtained in the breach, leaking information about Orange and their clients. The incident affected several third parties, among which ATR Airlines saw airplane schematics go public.
Apart from financial loss, Orange had to deal with reputational damage, as it needed to rebuild its trust capital among corporate entities.
Financial Services
Companies offering financial services are also attractive targets for ransomware attacks for several reasons:
- Higher potential for payouts
Companies in the financial field have strict Know Your Customer (KYC) processes, which means that they work with large amounts of data about their corporate and individual clients, partners, and employees. This is extremely attractive to bad actors, which deploy double-extortion attacks, where they steal data and encrypt essential systems. Financial institutions can’t exist without trust, so this approach increases attackers’ chances of hefty ransoms.
- Wider attack surfaces
With the emergence of artificial intelligence, cloud technologies, and data analytics, financial companies are gradually turning into fintech companies. Digital is not a layer anymore but a strong pillar on which these institutions base their strategies. In this context, the attack surface constantly increases.
To offer clients instant transactions, user-friendly interfaces, and smooth experiences, financial companies are changing their digital infrastructures, collecting more data, and sharing all this information with third-party vendors. This makes organizations in the industry exposed to attacks on their systems and on their providers.
- Difficulties in securing digital assets
Financial companies are constantly updating their systems to keep up with the industry’s and consumers’ needs. This puts pressure on the company and its employees, who need to be trained regarding usage and challenges.
With foreign exchange company Travelex, everything started with its Pulse Secure VPN server vulnerabilities that took months to patch. This offered attackers several chances of deploying Sodinokibi (or REvil), a ransomware-as-a-service (RaaS) model that targeted their Windows systems. The group encrypted essential company files, making the Travelex websites in 20 countries go offline.
The company that processes over 5,000 transactions an hour had employees perform tasks manually. Moreover, its global banking partners, which count worldwide known brands like HSBC, Tesco, and Barclays, couldn’t make foreign currency transactions. The group of cybercriminals requested a ransom of $6 million.
Government
Government institutions all over the world are at high risk for ransomware attacks. In 2020, organizations in the U.S. government registered recovery costs and downtime of almost $19 billion. 2021 followed on the same note, as American institutions suffered 79 attacks that impacted over 70 million citizens.
In this context, governments need to understand the risk and why they are such interesting targets.
Top Reasons Why Governments Are Ransomware Targets
Valuable, top-secret information
Cybercriminals’ interest in government information is significantly more substantial and diverse. This is because state institutions hold data on several key elements:
- Citizens, residents, and travelers;
- Military strategies and activity;
- Terrorist groups, potential terrorists, criminals, etc.
- Under-cover agents;
- Foreign policy and national security issues.
Bad actors target government information because they may sell it to nation-states for intelligence purposes, to political parties, activists, or other cybercriminals with their unique agendas and tasks. Of course, some actors may hold governments accountable and ask for payouts in return for their data and system access.
Extensive attack surface
Governments have up to millions of people working on their projects, many emails and terminals, cloud applications, servers, and login data that cyber attackers may exploit. Bad actors can enter systems and compromise their security by accessing just one exposure.
In addition, legacy systems that are still operated at the state level and third-party risks coming from partners and vendors increase the chances for cybersecurity attacks to be successful.
Critical infrastructure
Regional and local institutions operate critical services and infrastructure, such as railroads, transportation, power supply, communications, etc. The disruption of such critical systems would profoundly affect people’s lives and local economies. This is another reason why cybercriminals target state institutions.
Why Are Ransomware Attacks So Successful?
The Ransomware-as-a-Service Model
Similar to software-as-a-service (SaaS), ransomware-as-a-service (RaaS) requires users to pay for access to specific tools and services that specialized parties have deployed. This way, affiliates may launch attacks without owning or developing the software. This leaves them more time to focus on choosing their targets, distributing the malware, and pressuring victims.
RaaS works based on monthly fees or requires a commission of the profit for each cyber attack. The financial conditions are detailed in the license agreement. After accepting all terms, the affiliate gains access to the software and the onboarding information.
Some of the world’s top RaaS organizations include:
- DarkSide/BlackCat/ALPHV
DarkSide uses phishing emails with embedded links and malicious attachments to exfiltrate data. After attacking the U.S. Colonial Pipeline and making worldwide headlines, the organization disappeared, its servers were seized, and its crypto funds were emptied.
DarkSide is said to have rebranded as BlackCat/ALPHV, a group formed by many of its former developers. The new cybercriminal group has a more sophisticated approach to ransomware. They deploy several encryption strategies, spread between terminals, kill virtual machines, and take measures to ensure recovery is not possible.
- REvil/Sodinokibi
REvil uses phishing, brute-force attacks, and server exploits to capture and encrypt data. Moreover, the group also operates a leak site that enables affiliates to post data to persuade victims to accept bigger payouts and make payments faster.
REvil differentiates itself from similar RaaS organizations through the extremely well-designed features that enable cybercriminals to escalate privilege. Moreover, the group’s solution uses a system that takes computers into Windows Safe Mode and encrypts essential documentation and files.
- Conti
Conti uses a multitude of attack vectors, including stolen or cracked remote desktop protocol (RDP) credentials, phishing emails, and software vulnerabilities. It encrypts information using a unique AES-256 encryption key per file. This RaaS model gained its place as a top preference for cybercriminals, helping them extort several million dollars from over 400 organizations.
- LockBit
LockBit, with its most recent version, LockBit 2.0, uses double-extortion techniques. The solution employs Active Directory (AD) group policies to encrypt devices across Windows domains. Moreover, the group owns a dark web directory where affiliates may list their victims and the remaining time before exposing their data.
- Maze/Egregor
Maze has long been an innovator in the RaaS ecosystem and developed specific leaks and double-extortion tactics that other organizations later adopted.
In 2020, the group rebranded into Egregor and adopted a new approach, which mirrors Conti’s. Their affiliates use phishing emails containing malicious documents that drop the Qakbot worm. In addition, to ensure more robust initiatives, they double them with RDP approaches.
Double or Triple Extortion Attacks
To increase their chances of success, cybercriminals also employ double and triple extortion techniques.
With double extortion ransomware, attackers start by exfiltrating and encrypting valuable company data. Then, they use the information they collect to extort victims, putting pressure on them so that they pay the ransom.
Although the deal between victims and attackers is that, once the ransom is paid, any trace of the attack is deleted from the cybercriminals’ servers, there have been cases that proved otherwise. The Conti ransomware group, for example, is known for leaking data after their victims pay ransom.
A triple extortion ransomware attack goes even further, affecting third parties or associates. Bad actors demand payments from other parties, usually the actual owners of the sensitive data, to generate additional income flows.
For example, in 2020, Vastaamo, the Finnish mental health center, was hit by a triple extortion ransomware attack. The cybercriminals extorted not only the center’s representatives but also their patients, threatening to make available their medical records and, thus, share extremely private information.
How to Protect against Ransomware Attacks
1. Email Authentication Techniques
By deploying email authentication techniques, security teams can better protect their organizations against ransomware attacks. The most common controls they can use are SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance).
SPF (Sender Policy Framework)
SPF filters emails based on their sources. Using DNS records, the Sender Policy Framework sets which domains may be trusted and, thus, rejects those from non-trusted sources.
DKIM (DomainKeys Identified Mail)
Due to public-private key cryptography, DKIM checks incoming emails and their domains and stops messages that appear to be illegitimate.
DMARC (Domain-based Message Authentication, Reporting, and Conformance)
DMARC brings together the benefits of SPF and DKIM. This technique identifies fraudulent emails. Moreover, it defines the policies and steps that organizations need to implement when suspicious emails are detected. With Domain-based Message Authentication, Reporting, and Conformance, organizations may know what infrastructure the email sender uses and whether to accept the message, ignore it, quarantine it, or reject it.
2. Machine-Intelligent Email Security
Nowadays, machine intelligence plays a crucial part in cybersecurity strategies. Machine-intelligent email security solutions learn from the entire email activity within an organization. This means they understand who usually emails who, at what intervals, what types of messages get sent, and what they contain (attachments, links, etc.). Emails that deviate from the norm will be flagged and stopped before they even reach employee inboxes.
These solutions understand human communication behavior and relationships, and can thus provide complete protection against the full spectrum of email threats. They can proactively defend against zero-day, socially-engineered phishing attacks that are getting past traditional email defenses.
3. Security Awareness Training
Cybersecurity tools and technologies are crucial, but they can only protect an organization to a certain extent. What people do, the way they assess risk, their capacity to recognize suspicious activity, and how they respond to it are of the essence for any company trying to protect itself, its data, and its stakeholders.
This is where security awareness trainings are needed. Such initiatives educate employees on the types of ransomware attacks, common phishing techniques, how to inspect specific messages, and what to avoid.
Security awareness training is often done by organizing ongoing events, deploying internal initiatives, or sending out educational materials, like company newsletters.
Several rules make security awareness training successful:
- It is the company’s responsibility. Organizations need to provide information to their employees because they bear the responsibility of storing customer and partner data.
- It has to be consistent. Employees need constant reminders of how cybersecurity works, its importance, and the measures they need to take to keep their devices and accounts protected. Moreover, because organizations always recruit new people and change teams, onboarding should include a cybersecurity component.
- It has to be relevant and target different groups of people with different information. For example, executives need to undergo more in-depth training since they are more known and visible, and the risks associated with these positions are usually higher.
Successful organizations respect the rules above and go that extra mile to understand their employees’ behaviors. They often simulate phishing or spear phishing attacks to see how users respond. Based on the results of these simulations, they make organizational decisions and create and deploy the necessary strategies. Moreover, these initiatives offer a high degree of transparency, which means that specific employees may receive additional support.
4. Multi-Factor Authentication
Multi-factor authentication (MFA) is another effective way of protecting against ransomware. With MFA, bad actors need more than just credentials to access a specific account or network. Multi-factor authentication adds a layer of protection to the login process, working as an alarm system for attackers. The different types of MFA include:
Multi-factor authentication based on phone or email confirmations
Phone and email-based MFAs aren’t foolproof, but they offer additional protection. The issue is that once attackers have access to the email login credentials, they also have access to the MFA code. Compared to this option, SMS-based MFA is safer. Still, as bad actors are mastering SIM-card cloning and SIM-card re-issuance following impersonated requests to providers, organizations need to pay extra attention to multi-factor authentication.
Multi-factor authentication based on authenticator apps
Google and Microsoft offer Authenticator apps, usually installed on mobile phones. When trying to log in to an account, the user receives a code through the app. This approach is significantly safer than phone or email-based MFA, but it might still be compromised by attackers using fake-destination login websites.
Multi-factor authentication based on hardware security keys and biometrics
Multi-factor authentication based on hardware security keys and biometrics is the strongest form of MFA. Hardware security keys protect against attacks by leveraging cryptography. They verify users’ identities and the URLs of the login pages, offering the highest level of identity assurance.
5. Extended Detection and Response (XDR) Solutions
The current environment offers many employees the chance to work flexibly, from any location they want. This raises cybersecurity challenges, making unsecured remote desktop ports an entry point for ransomware attacks. Disabling or controlling these gateways carefully decreases the risk associated with compromising devices and lateral movement, which are vital attack pillars. This is done through cybersecurity solutions that monitor endpoint activity, ensuring centralized remote control.
With Endpoint Detection and Response (EDR) solutions, security professionals can collect continuously, in real-time, endpoint data and apply automated analysis and response principles to mitigate risks. EDR tools expand their actions beyond affected endpoints to reduce the attack surface, as they also scale their measures toward any vulnerable endpoint.
Extension Detection and Response (XDR) works similarly to EDR while offering increased support that expands to the computer infrastructure. XDR analyzes email sending and receiving infrastructure, servers, network devices, cloud solutions, and apps to identify risks and aggregate threat signals. These alerts are prioritized according to their risk levels.
Moreover, XDR uses threat intelligence to assess any connections between potential attacks, thus providing a more complex overview of emerging threat vectors.
Ransomware attacks are a challenge for security leaders and organizations worldwide. While industries like healthcare, manufacturing, telecommunications, and financial services are some of the most targeted, any company can become a target.
To mitigate risk and reduce their attack surface, organizations can use machine intelligence security solutions, email authentication techniques, MFA, and XDR. Still, for all of these to work and deliver results, companies need to invest resources in informing and educating employees through security awareness training. By preparing people and raising awareness of ransomware threats, organizations can greatly limit the chance attackers will be successful.
