Data exfiltration: Most common techniques and best prevention tactics
When cybercriminals target organizations, the goal is usually to exfiltrate information for competitive, disruptive, or monetary gain. Infiltrating a network or a device is not enough to make an attack successful; that only happens if the attackers successfully steal or remove data from the system.

Data exfiltration is a malicious process whereby cybercriminals (e.g., external actors) or insiders (e.g., employees, contractors, and third-party suppliers) accidentally or deliberately steal or move data from inside to outside a company's perimeter without authorization.
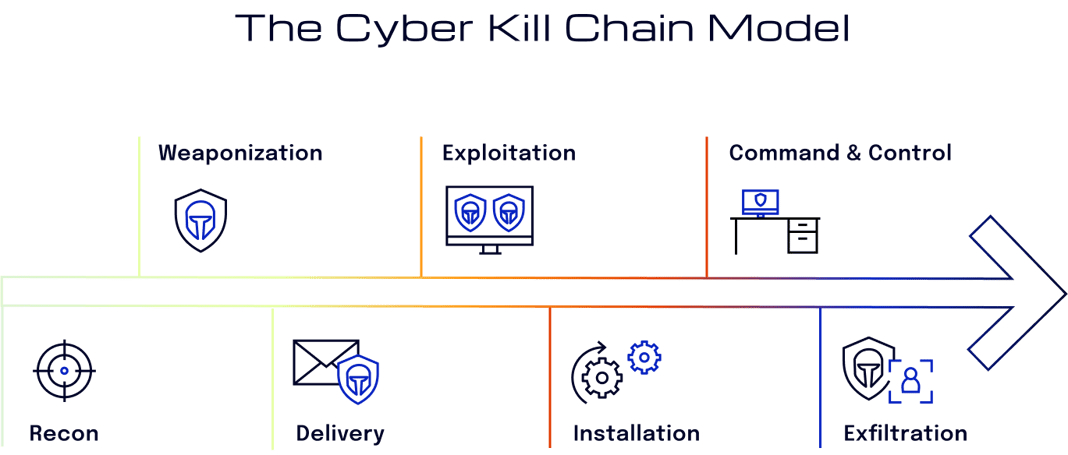
The Cyber Kill Chain model by Lockheed Martin
There are many data exfiltration techniques, but it is often done either physically or digitally. In most cases, it is performed via email, such as phishing. Data can be employee information, customer databases, intellectual property, payment card details, Personally Identifiable Information (PII), or other financial information.
No matter what form it takes, data exfiltration creates severe consequences for businesses in any industry. Failing to mitigate against data exfiltration and exercise as many preventative measures as possible can lead to:
- loss of intellectual property and other sensitive information
- expensive incident response processes
- information misuse or abuse
- violation of industry standards and regulations
- lawsuits and other legal issues
- reputational damage
Sufficient protection is becoming an increasingly more challenging task for security leaders due to two main reasons. First of all, cybercrime has evolved from an individual’s act to an organizational undertaking. Attackers now have the budget, resources, and sophistication needed to advance their data exfiltration methods. Furthermore, an organization’s data infrastructure contains several means—originally designed for the legitimate exchange of data—that can be used for data exfiltration.
Most Common Data Exfiltration Techniques
1. Inbound Email
With more than 300 billion emails sent per day globally, it is not surprising that email is the top vector for data exfiltration attacks.
Outsider Threats
A prime category of data exfiltration actors is malicious outsiders. External actors attempt to access a company's sensitive data to compromise it. Cybercriminals carry out attacks primarily using social engineering techniques, such as:
- Phishing
- Piggybacking/Tailgating
- Water Hole
- Scareware
- Dumpster Diving
- Shoulder Surfing
- Pretexting
- Honey Trap
- Baiting
- Diversion Theft
- Whaling
- Impersonation
Social Engineering and Phishing Attacks
Phishing emails are one of the major vectors of choice for malicious outsiders to distribute malware and exfiltrate data. According to Bolster's 2022 State of Phishing & Online Fraud Report, around 10.7 million phishing and scam pages were detected in 2021. Verizon's 2022 Data Breach Investigation Report found that phishing is a significant cause of 36% of data breaches. In addition, among 5,200+ confirmed data breaches, 82% of them involved the human element, including social engineering, misuse, and errors.
Using deceptive, manipulative social engineering techniques, attackers make their emails look legitimate and appear to be from trusted senders. Users are then more likely to click on a link or download an attachment that actually exposes the organization’s system to some malicious tool or malware.
In other cases, attackers might launch targeted phishing attacks to steal credentials from a specific user, such as senior company executives. Once they’ve tricked the user into providing their credentials, the attackers can use these credentials to take over the account, gain insider access, and ultimately exfiltrate data.
2. Outbound Email
Insider Threats
An insider threat is a cybersecurity risk originating from the targeted company. Insider attacks occur due to employees, contractors, vendors, partners, and third-party suppliers who accidentally or deliberately compromise data.
Accidental data theft occurs on account of oversight or negligence. For example, a negligent employee can email their company's private data to third-party suppliers. In the case of malicious insiders, a person deliberatively moves data from inside to outside the organization's perimeter.
Through outbound mail, attackers transmit sensitive data from secure computers to insecure private systems using authorized telecommunications infrastructures, such as company phones or business email accounts. The data can be attached as a file or transmitted as a text message or plain text email. This technique is most often used to steal source code, calendar data, images, business forecasts, databases, and company emails.
In addition, many email and messaging platforms automatically save drafts to the cloud. This means that someone who has outside access to their business email or other messaging service that supports saved drafts can exfiltrate information using that feature.
3. Downloads to Insecure Devices
These scenarios occur when a user accesses information through an authorized channel and moves the data to an insecure local device. For example, someone can use cameras, computers, smartphones, or other specialized devices to capture data for exfiltration, either downloading existing files from cloud services or copying the information into new files. Any files transferred to an insecure device are at high risk for data exfiltration.
4. Uploads to External Services
Like the previous technique, this method usually includes downloading sensitive information to local infrastructure. A user then uploads that data to a third party through a web browser client or some other unmonitored software. The third-party service could seem harmless, such as a social network, where someone could accidentally paste the wrong text or upload the wrong image.
5. Insecure Cloud Behavior
Cloud services introduce additional exfiltration risks to be aware of, including cases where employees or administrators use features of the provider in insecure ways. Any actor with the ability to deploy code, modify virtual machines (VMs), or make requests to cloud storage has the potential to exfiltrate data. Also, actors with sufficient permissions can transmit data from secure containers to insecure ones, or create unauthorized services on the company’s behalf.
How to Prevent Data Exfiltration
To prevent data exfiltration and consequences such as financial loss, compliance issues, and reputational damage, companies must identify and mitigate potential risks without harming user productivity. Anything less can leave them exposed. The following sections delve into some best techniques used to prevent data exfiltration.
1. Detect and Stop Phishing Attacks
Phishing is a successful means of attack because cybercriminals know how to take advantage of human error and how to bypass insufficient security solutions. Some organizations use some less-effective and traditional schemes such as blocking domains, Security Email Gateways (SEGs), and Rule-Based solutions. These signature-based methods cannot protect against highly personalized, low-volume, targeted attacks that do not include any identifiable malicious content.
Today's socially-engineered attacks often do not contain any traditional indicators of compromise. The best way to protect against email threats is to detect and stop fraudulent emails before they reach employee inboxes. Machine-intelligent email security solutions can learn from and understand the local context, communication relationships, and behavior patterns within an organization. They can identify any subtle deviations from typical behavior and stop targeted, socially-engineered attacks that traditional email security systems fail to detect.
2. Deploy Data Loss Prevention (DLP) Strategies
Data loss prevention (DLP) is a set of business policies and technologies designed to ensure end-users cannot send sensitive or confidential data outside the organization. This type of system scans all outbound emails, monitoring them for pre-determined patterns that might indicate a person is transmitting sensitive information, such as a credit card number or social security numbers. Depending on the policy, if an email contains text that matches this format, the program automatically encrypts the data or blocks it from being sent.
3. Disable Unauthorized Channels and Protocols
It’s essential for an organization to keep track of which users have access to their sensitive data, revoking access to any partner or employee after terminating a business relationship with them. Allowing someone to keep access even for one more day could lead to a security breach with severe productivity, reputational, or monetary consequences.
4. Implement Backup and Data Encryption Processes
If a security breach occurs, it is vital to be prepared and frequently back up all data so it’s available for quick restoration. Failing to regularly back up data can lead to significant loss, should the worst happen. Data backup is a cybersecurity standard requirement.
In addition, establishing encryption policies helps keep data safe while in transit. Cybercriminals cannot intercept or tamper with encrypted messages. Once confidential data is transformed into ciphertext, it needs a unique key to be unlocked.
5. Educate Employees
Finally, organizations need to minimize the risk of human error. Employees can make mistakes that attackers can leverage to their advantage. A user could unsuspectingly download an infected malware file, transmit their credentials through a phishing campaign, or otherwise neglect to secure their personal computer or other devices.
It is essential to regularly train and educate employees on the latest security measures to avoid human error. For example, organizations should ensure that each person understands how to identify a suspicious email. They should also make sure employees know how to report a suspicious email so the security team can investigate and take any necessary action right away.
All employees must be mindful of how to perform their security tasks effectively, such as knowing what to do and what not to do. To ensure appropriate security, organizations must educate their employees on topics such as:
- Clean Desk Policy
- Compliance with Laws, Standards, and Best Practices
- Data Handling, Labeling, and Disposal
- Policy on Bring-Your-Own-Device (BYOD)
- Personally Identifiable Information (PII)
- Safe Internet Habits
- Smart Computing Habits
- Password Behavior
- Email Threats
- Social Engineering
Cybersecurity threats continue to increase exponentially, and data exfiltration is a primary concern of businesses today. Traditional security controls are no longer sufficient to keep malicious attempts at bay. Therefore, security leaders should equip employees with advanced cybersecurity training and awareness to thwart the possibility of human oversight and error. In addition, they should deploy the necessary Data Loss Prevention (DLP) strategies, disable unauthorized channels and protocols, and implement backup and data encryption processes within their organization. Equally important, they need to deploy machine-intelligent email security solutions that are able to automatically detect and stop anomalous and malicious activity like data exfiltration attempts and targeted phishing attacks.

