How to protect businesses against supply chain attacks
In December 2020, FireEye announced that bad actors had infiltrated its network, revealing how extensive the fallout can be from a supply chain attack. In this case, a campaign of Russian espionage compromised the supply chain of IT management firm, SolarWinds. The group was then able to infect organizations like Microsoft, the US Justice State Department, and NASA, and gain potential access to as many as 18,000 SolarWinds customers across different industries, including large consulting, telecom, tech, and governmental institutions.

The SolarWinds attack is one example of many highlighting the risks that come with a complex supply chain and increased interdependencies between companies across industries. According to The State of Ransomware 2020 report, nearly one in 10 ransomware victims (9%) declared that the attack started with a trusted third-party supplier. 2021 saw a 650% increase in supply chain attacks, and this growth is expected to continue through 2022 and beyond.
To protect their organizations against the significant cyber risk that third-party expansion introduces, security leaders need to adopt and deploy the right security strategies. The first step is to understand the critical elements of a supply chain attack, how they unfold, and learn from the most damaging cases.
How Supply Chain Attacks Work
The supply chain is a complex ecosystem that involves everything from a company’s processes and procedures to its resources, employees, partners, and vendors. This environment is powered by software and hardware resources, cloud or local storage, web applications, e-commerce platforms, and other distribution mechanisms, and the software that manages their activities and contributes to delivering products and services.
Looking at the elements of the supply chain, one could differentiate between the two main entities (usually companies, groups, or other forms of organizations) and their assets (employees, documentation, financial, software and hardware resources, etc.):
- the Supplier (which offers a product or service to the beneficiary)
- the Supplier Assets (relevant components used by the supplier to deliver the product or service)
- the Customer (the end-user of the product or service)
- the Customer Assets (relevant elements that the end-user owns and uses to access and benefit from the product or service).
In a supply chain attack, there are two (or more) victims: an intermediary one, and the actual target. Such an attack first affects the supplier to access its networks and assets. Once infiltrated there, bad actors target high-value customers or other suppliers. They usually infiltrate smaller companies and use them as gateways for their target enterprises.
Stage 1: Hunt & Infect
In the first phase of a supply chain attack, cybercriminals identify vendors that work with businesses that store or use sensitive data. The objective here is to open a door that leads to even more opportunities.
Cybercriminals can attack the vendor through different means, exploiting aspects like lack of email security and unknown or unresolved vulnerabilities in the company’s software. Once in the system, they can add corrupt code to the company’s source code or insert malware. This way, they ensure that the next time an update is installed, the malignant code is delivered to all the company’s partners and connections.

Stage 2: Spread & Wait
In the next stage, once the malware is spread, bad actors simply need to wait. The software developers and vendors are not aware that their apps have been infected and will release the updates as planned. Since the new code comes from a trusted source, business partners and clients will acknowledge and accept it. Bad actors can then use the code as a backdoor to install ransomware on an infected network, or they can use it to collect sensitive information like credit card numbers or login information.
Stage 3: Attack & Collect
In the case of a state-sponsored attack, cybercriminals want to keep their presence unknown to gather intelligence. But if the attackers' focus is on the ransom, they will use the backdoor supplied by the third-party vendor to infiltrate additional networks and ultimately gain access to email addresses, login credentials, and other forms of PII (personally identifiable information). Once they do, they usually threaten victims that they can either seize and encrypt the sensitive data they find, or they can leak it. In both cases, the potential impact can be devastating for companies without a reliable backup strategy.
Types of Supply Chain Attacks
1. Software Supply Chain Attacks
A software supply chain attack happens when a bad actor infiltrates the network of a software vendor. Once there, the attacker employs malicious code to compromise the software before the vendor sends it to their customers.
Three of the most common techniques to execute software supply chain attacks are:
Hijacking Updates
Software products come with constant updates which help introduce new features, repair bugs, and enhance the overall experience. This routine part of product maintenance is typically done through centralized servers that distribute the updates. Bad actors can hijack an update to insert malware in the coming update or alter the update to gain control over the software’s functionality.
An example of a well-known update hijacking is the NotPetya attack. In 2017, a team of bad actors directed their efforts toward Ukrainian companies and spread malware through one of the most used tax accounting software programs in the country. The attack generated an echo in Ukraine and beyond, affecting companies worldwide and disrupting international shopping, financial services, and healthcare operations internationally.
Undermining Code Signing
To protect code and verify its integrity and authenticity, authors use code signing, a digital signature that may be placed on everything from files to software updates and executables. Cybercriminals can undermine code signing by either signing the certificates themselves, breaking the signing systems, or exploiting accounts with weak protection. Undermining code signing allows them to hijack software updates by impersonating a trusted third-party and inserting malicious code into an update.
Compromising Open-Source Code
Sometimes, developers search for publicly accessible blocks of code to perform specific functions. Bad actors can exploit this approach and compromise open-source code by inserting malicious code into libraries that are easily and freely accessible.
In 2017, researchers found that 12 of the Phyton libraries uploaded on the Python Package Index (PyPI) included malicious code. When used, the code delivered the functionalities developers were looking for and provided additional, unsolicited features that enabled bad actors to open reverse shells on terminals or obtain boot persistence.
2. Vendor Email Compromise
Vendor email compromise (VEC) is one of the most sophisticated forms of business email compromise (BEC), an attack in which a cybercriminal tricks executives and employees into making payments or sending sensitive data to fraudulent accounts. In the case of VEC, attackers take over a recognized vendor’s legitimate email account in order to defraud the company and its employees, clients, or partners. These attacks are becoming more and more common with every passing year. Compared to 2020, 2021 saw a 156% increase in the number of companies that had faced a VEC attack.
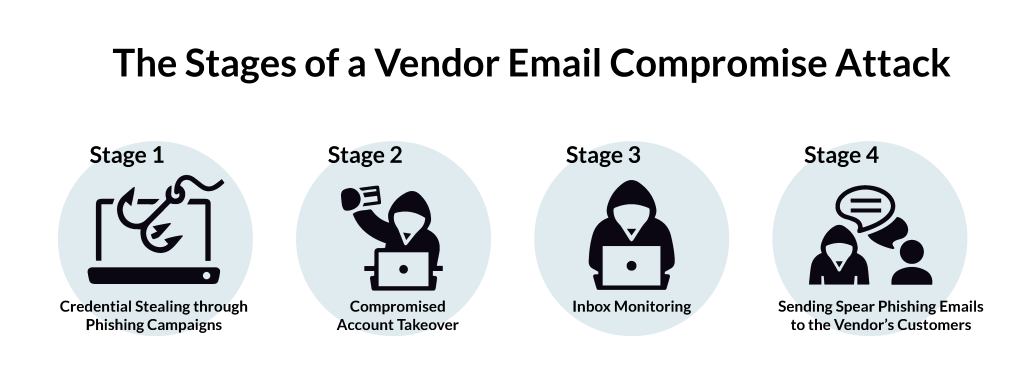
Stage 1: Credential Stealing through Phishing Campaigns
Bad actors first need to infiltrate the vendor’s email accounts. The most common way of doing so is through phishing. After identifying a list of potential targets, they send fraudulent emails to employees, many of which contain malicious links. An unknowing employee may open the link or provide their credentials without checking if the sender and landing page are legitimate. This behavior allows bad actors to infiltrate the company network and move forward with the attack.
Stage 2: Compromised Account Takeover
Since, at this point, attackers have the necessary credentials, they can take over the email accounts and surveil communications. They will often create rules that auto-forward all emails to a mailbox created specifically for this purpose.
Stage 3: Inbox Monitoring
Successful VEC attacks usually take weeks, sometimes even months. Cybercriminals need to study the incoming emails, identify the vendors’ clients, how they communicate, the specific dates for deliveries, the frequency, format, design, and amounts for invoices. Moreover, they need to understand which employees are in charge of critical responsibilities, like sending invoices to clients. By paying attention to all these and ensuring their emails look and sound genuine, they increase their chances of success.
Stage 4: Sending Spear Phishing Emails to the Vendor’s Customers
After carefully monitoring communication, cybercriminals can launch the attack on the vendors’ customers, asking for payments. They pretend to be the vendors’ representatives and send customers spear phishing emails that follow the tone of voice and style with which potential victims are already accustomed. Since everything appears in place and the documentation looks legitimate, the employees may remain unsuspicious when cybercriminals ask them to send the money into a different account, citing changes or bank issues.
Get the Free Guide to Smarter Email Security
Everything you need to know to efficiently minimize email attack surface and stop modern attacks at first sight.
Significant Supply Chain Attacks That Started with a Phishing Email
Over 500 Companies Hit by Silent Starling
The West African cybercriminal group known as Silent Starling has been using phishing campaigns for years to steal credentials and defraud over 500 companies in the United States and over a dozen other countries.
In one instance, between September 2018 and March 2019, the group deployed 5 phishing campaigns targeted against a US-based company, and managed to compromise 39 email addresses of critical team members, from billing specialists, sales account executives, and HR employees, to branch managers and even a senior executive. Out of all these, 13 accounts fell victim to the phishing campaign in the first 30 minutes since deployment, showcasing the effectiveness of this approach. To steal credentials, Silent Starling would link phishing sites that resembled voicemail and fax notifications, as well as Microsoft OneDrive or DocuSign login pages.
Once they hijacked the email accounts of employees within the company’s finance department, the group would then monitor communication, gathering information and data about these mailboxes. They would then use this information to send fraudulent invoices to multiple companies.
Fortune 500 Electronics Company Data Exposed After Third-Party Breach
In February 2020, General Electric, a Fortune 500 electronics conglomerate, fell victim to a third-party data breach. A group of attackers managed to take over an email account of a key supplier, Canon Business Process Services, following a successful phishing attack.
On March 20, General Electric received a notification letter that announced the breach, mentioning that the Canon BPS attack exposed a considerable amount of personal data and documents of GE employees. The information included passports, driver’s licenses, birth certificates, direct deposit forms, tax and withholding forms, among others. Since this was highly sensitive data, it was extremely valuable in underground criminal forums, as bad actors could use it for more phishing attacks.
Trezor Cryptocurrency Wallet Holders Attacked After Mailchimp Compromise
On March 26, 2022, Mailchimp, the email marketing platform used worldwide, discovered that a group of cybercriminals had infiltrated its system after a successful social engineering phishing attack. While the company quickly deactivated the 300+ email accounts that had fallen victim to the breach, bad actors still managed to export the mailing lists of 102 accounts. They were thus able to target the users of Trezor, a hardware cryptocurrency wallet and one of Mailchimp’s clients, with sophisticated phishing emails, inviting them to download the newest Trezor Suite desktop app update. Once users clicked on the link, they were directed to a cloned app landing page that looked realistic. The fake was meant to steal users’ seed phrases.
How to Protect against Supply Chain Attacks
1. Assess Third Party Risks
To protect against supply chain attacks, an organization must first know its partners, collaborators, and connections, such as IT service providers, cloud providers, finance, legal, HR services, MSP / MSSP, etc. Putting together an exhaustive list will help security professionals identify the weak link—organizations with little or no procedures in place—and create and deploy the necessary strategies.
Once the list is made, organizations will also need to assess and acknowledge each company's access to their network. Adding that information offers one a clear view of where their company stands in terms of cybersecurity and how susceptible it is to supply chain attacks. Depending on what they discover during this audit, they may want to reduce their suppliers’ access to the minimum.
After listing all suppliers and their relationships with one’s network, it is important to understand their security postures and check if they are subject to any certifications or audits. Some companies, like payment processors or cloud suppliers, might be obliged by the law to comply with specific cybersecurity and data protection laws. In this case, an excellent way to ensure they respect procedures is to review the reports on compliance (RoC) issued by the responsible authorities. Another essential certification that applies to cloud service providers is SOC 2/2+/3. This focuses on the Five Trust Principles: privacy, security, availability, processing integrity, and confidentiality.
Apart from the above, organizations can benefit from asking their suppliers about GDPR compliance, previous cybersecurity incidents, data breaches, and penetration test reports. Moreover, their supply chain vetting processes should also include constant discussions with vendors to understand their challenges, plans, and how they keep up with cybersecurity threats.

2. Implement the Principle of Least Privilege (PoLP)
In addition, security professionals should reinforce PoLP, the Principle of Least Privilege, to protect systems and data. This approach tallies with Zero Trust frameworks, which are based on the premise that no one, inside or outside the organization, should be trusted and that users should be verified each time they are granted access to a system. The objective is to ensure that attacks are challenging to achieve and that one minor slip from a vendor doesn’t open the door for significant damage.
Implementing PoLP requires organizations to take several steps, such as:
- Auditing all accounts to identify privileged ones. This involves assessing all environments, from on-premise to cloud-based, DevOps and endpoints, checking SSH keys, access keys, and password hashes.
- Identifying users and their privileges to ensure that they only have access to what is necessary to deliver their work. Any unnecessary administrator privileges should be reduced.
- Differentiating access paths to separate standard and admin accounts and ensuring that the sessions of privileged users remain isolated.
- Ensuring that the credentials of privileged administrator accounts are secured in a digital vault.
- Consistently rotating administrator passwords, changing them instantly after each usage to mitigate risks associated with Pass-the-Hash and keylogging approaches.
- Monitoring administrator accounts activity to know what is happening at all times and, thus, identifying abnormal activity and potential attacks.
- Implementing just-in-time access elevation. This enables users to benefit from additional privileges on a time-limited window, according to each project’s needs.
- Conducting consistent reviews of IAM permissions and rights reviews in AWS, Azure, and GCP.
3. Ensure Continuous Security Awareness Training
People are an essential part of any organization. Protecting against supply chain attacks is not only related to technological assets and procedures imposed. The human defense is also important.
Employees need to be aware of the current threats and know how to identify a phishing email. They should also know what to do when things appear unclear and who to ask in case they fear a potential risk. This means that a company must have an internal communications strategy that focuses on informing and reinforcing cybersecurity principles through tactics that are deployed with regularity and target all staff members. Such an approach can include anything from videos to meetings, workshops, newsletters, and posters, among others. The more practical and to the point these techniques are, the easier it will be for people to understand the risks, retain what they need to do, and contribute to creating a culture of security.
4. Constantly Review & Update Security Operations Hygiene
Solid cybersecurity procedures can ensure that threats don’t escalate and turn into disastrous data breaches. Standard practices include:
- Enabling multi-factor authentication (MFA): An attacker's general approach is to steal credentials obtained through phishing initiatives and gain authorized access to the organization’s systems. When vendors aren’t obliged to use multi-factor authentication, these credentials can be enough to initiate an attack.
- Reviewing supplier privileges: Sometimes, companies offer vendors remote access technologies like VPNs and RDPs. When organizations don’t segment privileges according to the suppliers’ needs and responsibilities and don’t impose MFA, they increase their attack surface. To improve their security posture, they can limit the rights of vendors and use “jump hosts”.
- Monitoring supplier security bulletins: Sometimes, orrganizations expect to be notified when an attack has happened on a vendor, so they can then take measures. In many cases, that company may not be the first one on the list. Monitoring supplier security bulletins and keeping track of news headlines about vendors’ cybersecurity strategies is crucial. Proactivity is key because the sooner a company identifies risk, the sooner they can mitigate it.
5. Consider a Machine-Intelligent Email Security Solution
Examples of companies like Canon BPS and Mailchimp falling victims to phishing attacks showcase that, no matter how big the organization or how many resources it has, failures still occur. Because bad actors are using social engineering in their phishing attempts, and often without any identifiable malicious content, these highly personalized, low-volume, targeted attacks can easily bypass most current security controls. To prevent VEC, traditional email security solutions are no longer enough.

Machine-intelligent email security solutions like xorlab Active Threat Defense (ATD) can automatically tailor their threat detection engine to the behavior of any organization to identify and stop phishing and other emerging cyber threats at first sight. These solutions understand and learn from the local context, communication relationships and behavior within an organization, and can spot anything that deviates from the norm. By analyzing the attack surface of each email, assessing each relationship (person to person, person to organization, and organization to organization), and understanding human communication patterns, ATD can proactively defend against zero-day, socially-engineered phishing attacks that are getting past traditional email defenses.
With the right combination of technology, good security practices, and awareness training, security leaders will be able to mitigate the risk of supply chain attacks.

