Phishing on GitHub: A Sophisticated Attack Leveraging Brand Trust
During the last week there has been an uprise in phishing cases originating from GitHub, targeting software developers and members of the GitHub community. Given what we’ve discovered, we believe that the phishing attack represents an attempt to compromise GitHub user accounts, and potentially the first step of a software supply chain attack. This attack is an interesting showcase of how the brand, reputation, and infrastructure of a highly trusted digital platform is leveraged to bypass defenses and lure people into revealing sensitive information. We hope to provide meaningful insights to our readers to enhance awareness and preparedness against such threats.

Screenshots were anonymized to prevent leakage of personally identifiable data.
The Attack Vector: Exploiting GitHub's Notification System
The phishing attack starts with a well-written email informing the target about an exciting career opportunity. The call-to-action is a link to a website imitating GitHub’s job board and claims to lead to a form for completing the application process. The linked domain was registered very recently on 18.02.2024, two days before the email was received, and imitates GitHub’s real talent site https://www.githubtalentcommunity.careers.
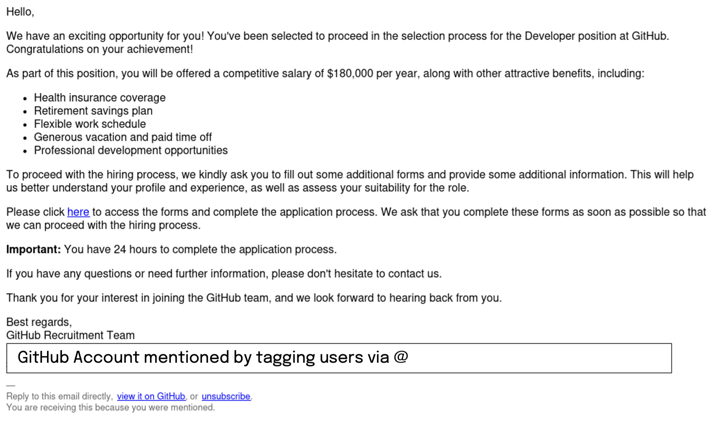
By following the link to the presumed GitHub Job board, one will be prompted to authenticate. This indicates that the goal of the phishing attack is to compromise GitHub accounts. As indicated in this thread, the attackers try to register an application accessing the GitHub accounts of the victims. By doing so, they can reuse the accounts to propagate the phishing scheme even further. However, the potential damage does not stop here. As the registered application has access to the complete account of the victim (i.e. all repositories, public and private), the attacker has full control of the resources tied to this account and can do whatever they want with them.
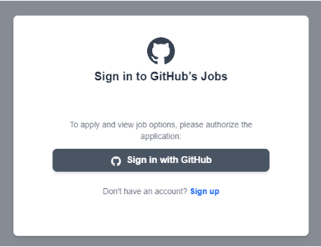
The email successfully bypasses all the standard filters, because it was sent through GitHub’s own email infrastructure therefore passing all authenticity checks (note that it did not pass through xorlab Security Platform). Since the email comes from GitHub directly, the attackers can leverage the reputation of the GitHub infrastructure and the trust people have in the GitHub brand.
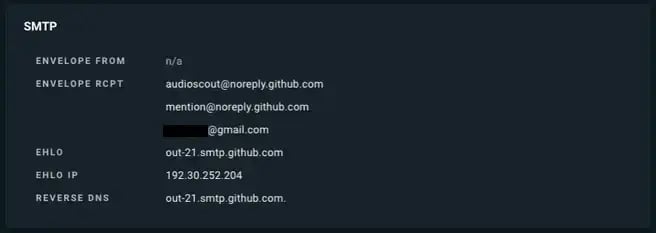
To achieve this, the attacker comments within GitHub and tags targeted accounts. The comments are made to a seemingly random issue or pull request and are tagging numerous GitHub users. This action triggers GitHub's notification system, which, in turn, emails the content of the comment to those tagged users, provided they have their notification settings configured to receive emails for @mentions and custom activities.
The interesting aspect of this phishing attack lies, as mentioned before, in the use of GitHub's infrastructure to lend credibility to the phishing attempt, as the notification email originates from GitHub's domain, a trusted source for most users. The feature of tagging other people in issues or pull requests is as intended and is also an important part of the way the community works on GitHub. The malicious usage of such, of course, is not intended.
Display Name Deception
Another critical element that adds a layer of sophistication to this phishing attack is the manipulation of the email's display name. Since GitHub's email notifications use the display name of the commenter (in this case, the account of the attacker), the attacker can basically choose what the name in the from field is in the phishing email. This level of customization in the phishing content significantly increases the risk of recipients being deceived by the apparent legitimacy of the email.
The following Message header shows the from field in the email which is corresponding to the the display name of the commenter above.
Detection of the Phishing Mails
One indication that this is in fact a phishing attempt and not a real job offer, is that the subject of the phishing email is referencing to the GitHub issue where the comment was made. Additional indicators are the sense of urgency by stating one has only 24 hours to react, no personal addressing of the email and of course a non-reputable domain for the link in the body of the email.
There are multiple domains used for this phishing scheme, all of which were registered only some days before the attack.
githubtalentcommunity [DOT] githubcareers [DOT] online
and
auth [dot] githubtalentcommunity [dot] online.
Immediate Measures
To mitigate the risk of falling victim to such phishing attacks, individuals and organizations are advised to exercise heightened vigilance, especially when dealing with unexpected job offers or urgent requests via email, even if they appear to come from reputable sources like GitHub. Additionally, GitHub users should review their notification settings, understanding that the configuration to receive emails for "@mentions and custom" activities can be exploited by attackers to deliver phishing content directly to their inboxes.
If an account in your organization got compromised, check the authorized OAuth App of the account in question via this link and remove all unwanted authorizations.
Additional Mitigative Measures
A compromise of GitHub accounts could also happen in another way, not only in this phishing scenario. Hence it makes sense to install procedures that are resilient to such compromise. In the case of GitHub, we recommend the following measures:
- Enable and enforce MFA for all GitHub accounts in your organization
- Build development processes including merge request reviews to prevent the introduction of malicious code by a single person
- Build awareness for phishing and consider targeted awareness campaigns for developers and technical staff in general
- Prevent secrets from entering repositories, including private repositories
- Introduce commit signing via ssh keys.
Conclusion
This phishing technique underscores the importance of continuous education and awareness in the cybersecurity domain. Attackers are increasingly creative, exploiting trusted platforms and their mechanisms to conduct sophisticated phishing campaigns. By understanding the methodologies employed in these attacks, security professionals can better prepare and protect their organizations against the ever-evolving threat landscape.
For a deeper understanding of this specific attack and to view evidence of the phishing content, refer to the discussion on GitHub's community forum here.
Attacks like this show that traditional email security controls are increasingly challenged to keep employees safe.

