How to identify and prevent email impersonation attacks
Email impersonation is a phishing technique that involves using a fake email address that looks like a legitimate one. The attackers create email addresses and sender names with slight deviations to convince users that the message is genuine. They may impersonate the target organization’s employees, vendors, or business partners and trick the user to disclose sensitive information, such as intellectual property or payroll data, transfer money, or enter their credentials into a fraudulent website to steal their login information (credential harvesting).
The use of email impersonation is particularly common in:
- Business email compromise (the cybercriminal impersonates a business)
- CEO fraud (the criminal pretends to be a company executive)
- Whaling (the bad actor targets a high-level executive)
Email Impersonation vs. Email Spoofing
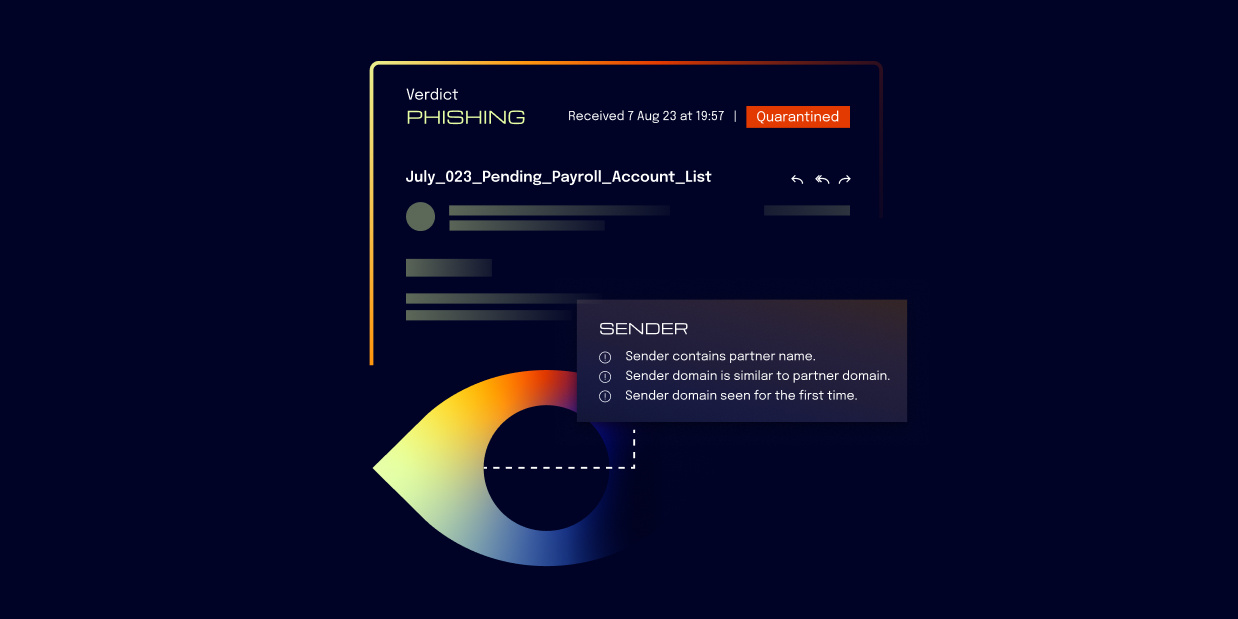
Although the two tactics are related, they are not quite the same. In email impersonation, the cybercriminal creates an address that looks like the real one. For instance, someone receiving the email may see an address that looks like customerservice@wells.farg0.com, which is similar enough to a real Wells Fargo address to seem legitimate.
In spoofing, the attacker changes the email’s header so that the message displays a false email address. For example, the cybercriminal’s address might be JosephHarris@yahoo.com but the user sees CustomerService@CapitalOne.com in their inbox.
Types of Email Impersonation
1. Root Domain-Based Impersonation
Most companies have a distinctive root domain that appears on every company email. Some examples are info@microsoft.com or customerservice@capitalone.com. In these examples, “microsoft” and “capitalone” are the root domains. In the case of root domain-based impersonation, cybercriminals create root domains that look like these legitimate ones by using replacement characters. On close inspection, a reader can see a minor change; for instance, a letter that's been changed to a number.
2. Top-Level Domain-Based Impersonation
The top-level domain is the part that denotes a country or the type of organization in a website or email address. Some common top-level domains are:
- .edu: Educational institution
- .org: Nonprofit organization
- .com: Business
- .gov: U.S. government agency
- .uk: UK-based company
- .de: German company
- .au: Australian company
Some impersonated email addresses have legitimate-looking addresses, but the top-level domains are different. For instance, the email address might end in the domain of a different country or type of institution. The address looks close enough that many people won’t notice it.
3. Subdomain-Based Impersonation
Most email addresses don’t have a subdomain, so this type of impersonation is less common. There are two main ways a cybercriminal can use the subdomain to create a false email address. One is by switching the domain and subdomain. For instance, instead of writing info@mail.microsoft.com, the cybercriminal may create an address that reads info@microsoft.mailerinfo.com, which might look legitimate but isn’t the actual company email or subdomain. In this case, “microsoft” is the subdomain, and “mailerinfo” is the domain. Another method involves splitting the company’s name across a subdomain and domain, like in info@micro.soft.com.
4. Display Name Impersonation
The display name refers to the way an email client shows a sender’s name. When someone creates an email account, they choose how they want recipients to see their display name. The name may not always match the username on the account. For instance, the username might be cmclinton123@outlook.com, but the display name looks to readers like “Microsoft Customer Services”, if that’s the display name the cybercriminal selected when setting up their account.
Some well-known email platforms only show the display name to recipients. The person getting the email doesn’t see the actual email address unless they deliberately look for it. This makes it easy to know who’s contacting a recipient, but it also makes it easy for attackers to impersonate a display name.
5. Username Impersonation
Username impersonation is one of the least sophisticated forms of impersonation, but unsuspecting recipients might still fall victim. In this case, the cybercriminal creates an email account with a name that looks like someone else’s email address. They may use Yahoo or other free email platforms to create these addresses. For example, if a company has an executive whose email address is Jennifer.Thompson@AceManufacturing.com, a bad actor may create one that’s Jennifer.ThompsonAce@yahoo.com.
How to Protect against Email Impersonation Attacks
With email still being the primary means of communication for businesses, it is important to protect against impersonation attacks and mitigate email security risks. Organizations looking to ensure comprehensive protection should focus on awareness training for employees and machine-intelligent security solutions that stop impersonation emails before they reach employee inboxes.
Employee Awareness Training
Employee awareness is critical to preventing email attacks. These are getting more sophisticated, and it can be difficult for employees to spot them. Security awareness training can address this issue.
This training should be detailed and customized to an organization’s needs. It can help employees learn the obvious signs of email impersonation:
- inauthentic top-level domains
- using a subdomain to imitate a company’s main domain
- false display names
- false usernames
- replacement characters in the root domain
Besides these signs of email impersonation, employees should learn to look for signs of social engineering. One common indication is the “urgent” email requesting immediate action.
Machine-Intelligent Email Security Solutions
Employing machine-intelligent email security solutions should be part of any comprehensive cybersecurity strategy. Employee awareness can only go so far. Traditional secure email gateways are a start, but they are not enough to protect businesses from targeted and sophisticated attacks. Machine-intelligent email security solutions provide organizations with the best possible chance of identifying and stopping email impersonation attacks. These solutions understand the local context, communication relationships and behavior within an organization and can spot the subtle distinctions that mark email impersonation.

